Blog post
Employment-Based Espionage: Foreign Fraud Threats to US Institutions
Dan Hildenbrand
Published
September 22, 2025
Much has already been written about how North Korean intelligence services have begun funding DPRK programs — including weapons programs – by infiltrating American tech startups posing as remote workers. But the scope of this threat goes way beyond just tech companies; the scale is much broader than some might imagine, and the methodologies employed in these schemes can be surprisingly complex.
American institutions both public and private must be vigilant (and accurate) in verifying to protect themselves and the American people against this threat. Let's take a look at two recent case studies to see why:
Case study: beyond employment fraud
On February 11, 2025, 50-year-old Arizona woman Christina Marie Chapman pleaded guilty to federal charges including "conspiracy to commit wire fraud, aggravated identity theft, and conspiracy to launder monetary instruments." She was sentenced to 102 months in prison and ordered to pay several hundred thousand dollars in connection with a fraud scheme the US Department of Justice says "exploited more than 300 American companies and government agencies" and generated more than $17M in revenue for the DPRK.
To accomplish this, she reportedly stole dozens of US identities, and she used them to do more than just apply for jobs.
For example, we investigated SentiLink application data related to Chapman and one particular identity that she stole: that of "BC" (not the identity's real name).
Over the course of the past five years, we can see applications coming in from the real BC. These applications list the same contact email address – one that has been associated with BC since at least 2006 – and mailing addresses in a California city that BC has been associated with since at least 2006.
But in 2023, applications in BC's name were submitted to various HR providers. One such application reviewed by SentiLink used BC's real name and DOB, but the email was brand new, the phone number was a VOIP number that had previously not been associated with BC, and the listed mailing address was an Arizona address linked to Christina Chapman. To submit this application, Chapman used a web proxy to make it look as if she was located in California. (SentiLink flagged this application as very high-risk for identity theft).
.png?width=915&height=482&name=Blog_Image_01%20(2).png)
That application likely reflected one of Chapman's many attempts to secure remote employment from an American company, in this case using BC's stolen identity.
But Chapman wasn't only using these identities for employment applications. In January 2024, for example, she used BC's identity again, this time in an application to a major credit union. This application listed BC's true address and also included her real Social Security Number. It listed the same email associated with the earlier applications to the HR providers, a VOIP phone number from the same provider seen on the previous application, and was submitted via a VPN server located in California close to BC's mailing address. (Again, SentiLink flagged this application as very high-risk for identity theft).
Although we don't know for sure Chapman's motives for using the stolen identity to attempt to open the credit union account, it stands to reason that people committing this sort of fraud might also want to open bank accounts in the same victim's name so that they have a place to direct payments from their new "employers."
These example applications are just the tip of the iceberg: per Acting Assistant Attorney General Matthew R. Galeotti of the Justice Department’s Criminal Division, "Chapman [...] exploited more than 300 American companies and government agencies" as part of her scheme to fund DPRK programs.
This is not a problem that just impacts tech firms. The good news is that these sorts of schemes can be prevented, or at least hindered, with more accurate fraud detection – SentiLink's Identity Theft Score flagged both stolen-identity applications as very high-risk.
Case study: synthetic identities and government institutions
In June of 2025, the US Department of Justice (DOJ) announced the indictment of several foreign nationals and one New Jersey man named Zhenxing "Danny" Wang for their roles in what the DOJ alleges was a scheme to fund the DPRK's weapons of mass destruction (WMD) program. This scheme involved using stolen identities to apply for US tech jobs, but again, looking at one of the SentiLink applications associated with Danny Wang reveals there's more to the story than just landing tech jobs with stolen identities.
For example, in 2023, applications were submitted to HR providers under the name "Jason." One such application reviewed by SentiLink lists a commercial mailing address in California and a California-based VOIP phone number, but was submitted via a device with a New Jersey IP address that SentiLink historical data links to Danny Wang.
But in this case, "Jason" doesn't appear to be a stolen identity. Rather, it seems to be a third-party synthetic identity – a completely fake identity that Danny Wang presumably invented. SentiLink's Fraud Intelligence Team was unable to find any history associated with this identity. It thus appears that in addition to stealing the identities of Americans, some North-Korea-linked fraud rings are also leveraging synthetic identities. (SentiLink's model scored the application as high-risk for synthetic fraud.)

This case, too, has implications that go far beyond US tech companies hiring remote workers. In the indictment of one of the co-conspirators, the DOJ alleges that as a result of the scheme, "false and misleading information" was transmitted not just to dozens of US companies but also to a variety of government organizations and federal agencies, including the Department of Homeland Security (DHS), the Internal Revenue Service (IRS), and the Social Security Administration (SSA). DHS, for example, operates the e-Verify service to verify employment records; this scheme resulted in inaccurate employment information associated with the stolen identities (and potentially also synthetic identities) being transmitted to DHS.
Getting this inaccurate information into government databases likely also makes this scheme easier in the future as (for example) a synthetic identity that is employment-verified with DHS is likely to have an easier time securing a loan.
Overall, DOJ alleges that the scheme generated at least $5M in revenue for the fraudsters and caused additional damage and losses of more than $3M for US companies and government organizations in "legal fees, computer network remediation costs, and other damages and losses."
Conclusion: how to catch foreign-backed employment fraudsters and protect American identities
While these two small case studies barely scratch the surface of the problem, they serve to illustrate that it is broader in scope and scale than many people realize. Fraudsters are leveraging both stolen and synthetic identities to fraudulently secure employment at US tech companies, but they're also using these identities to apply to other institutions, and their connection to employment means that false information often also ends up submitted to government institutions such as DHS, IRS, SSA, and could potentially impact state unemployment insurance agencies when the stolen or synthetic identities are fired.
The good news is that both case studies also illustrate that these schemes are not flawless. Many of these employment applications follow the same patterns we see in "traditional" fraud targeting financial institutions: stolen identities with brand-new emails, new VOIP phones, VPN or residential proxy IP addresses, etc. Comparing these data points against historical data associated with the applicant often makes the identity theft and other types of identity fraud obvious.
SentiLink's identity theft and synthetic fraud scores accurately identify high-risk applications in real time at the point of application – all of the applications discussed in this article were scored as high-risk by our models. Because we serve more than 400 US institutions across the public and private sectors and verify more than 3M identities every day, SentiLink has a deep well of historical data that allows our models to easily spot these inconsistencies – and a human Fraud Intelligence Team that's always deep in the trenches, researching the latest fraud MOs.
Reach out today to learn more about how SentiLink can help you protect American identities, reduce the threat posed by foreign nations leveraging fraudsters, and prevent fraud.
Related Content
.png)
Blog article
February 20, 2026
Romance Fraudsters Have Found a New Target: Your Home Equity
Read article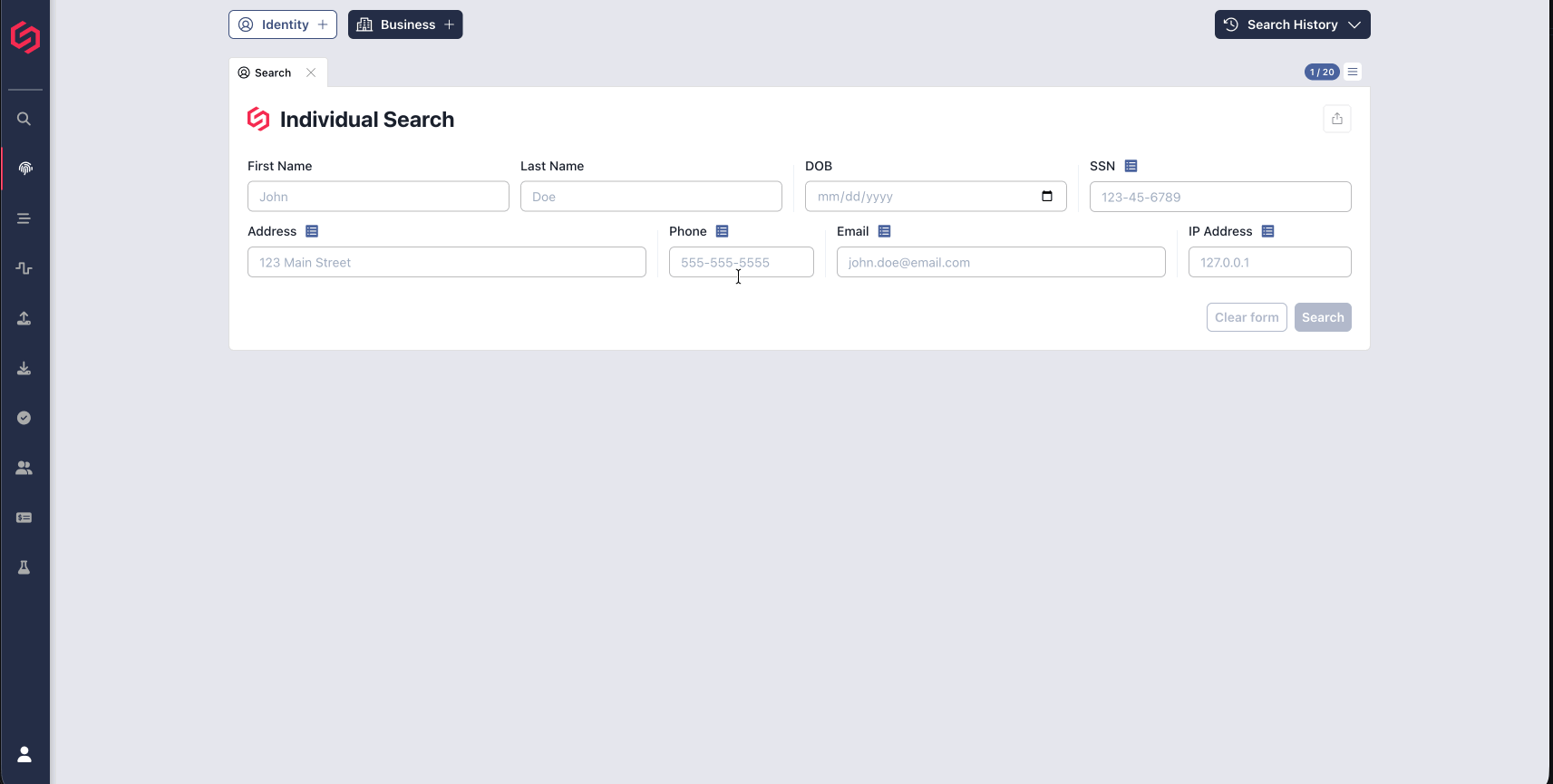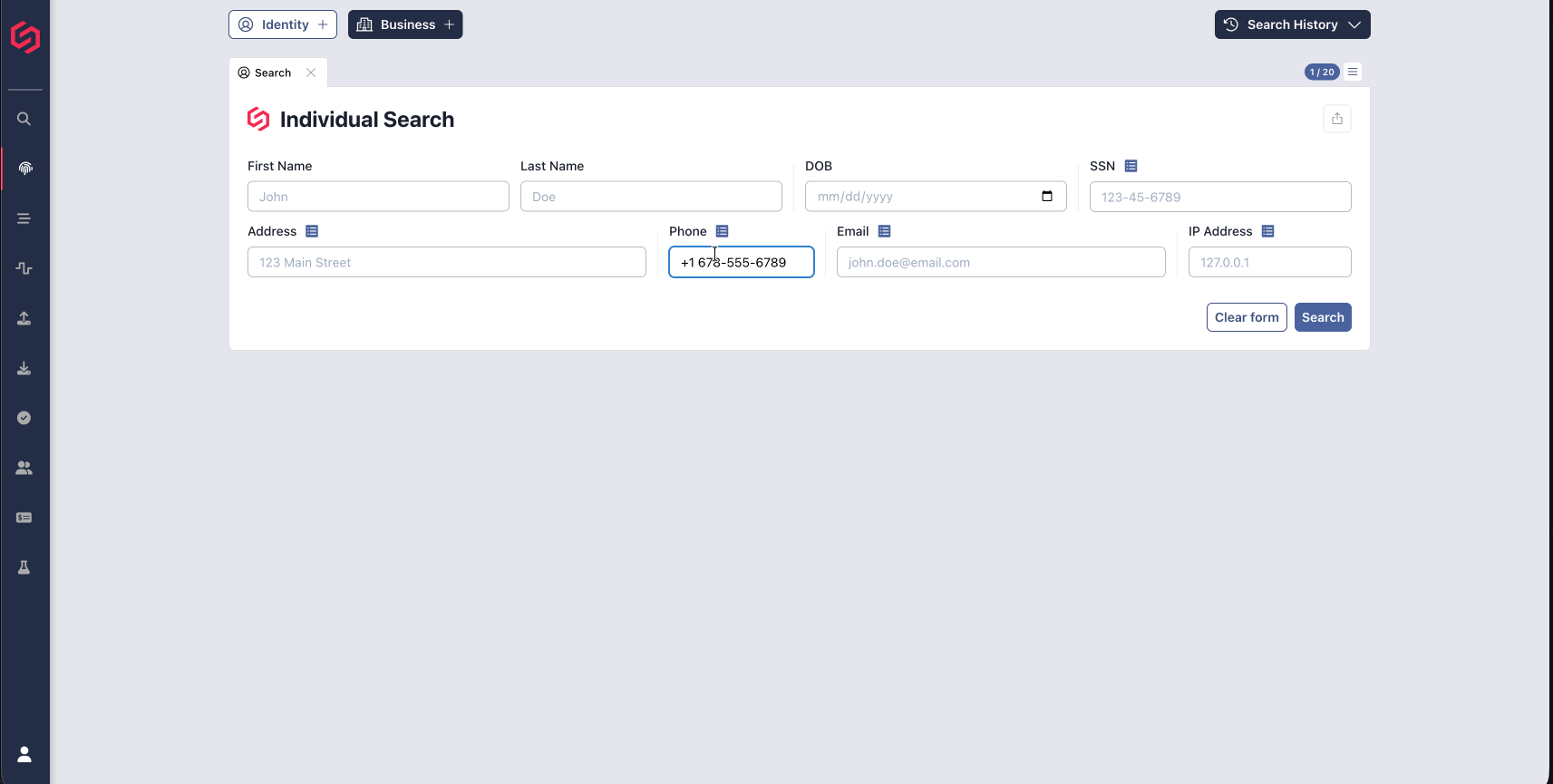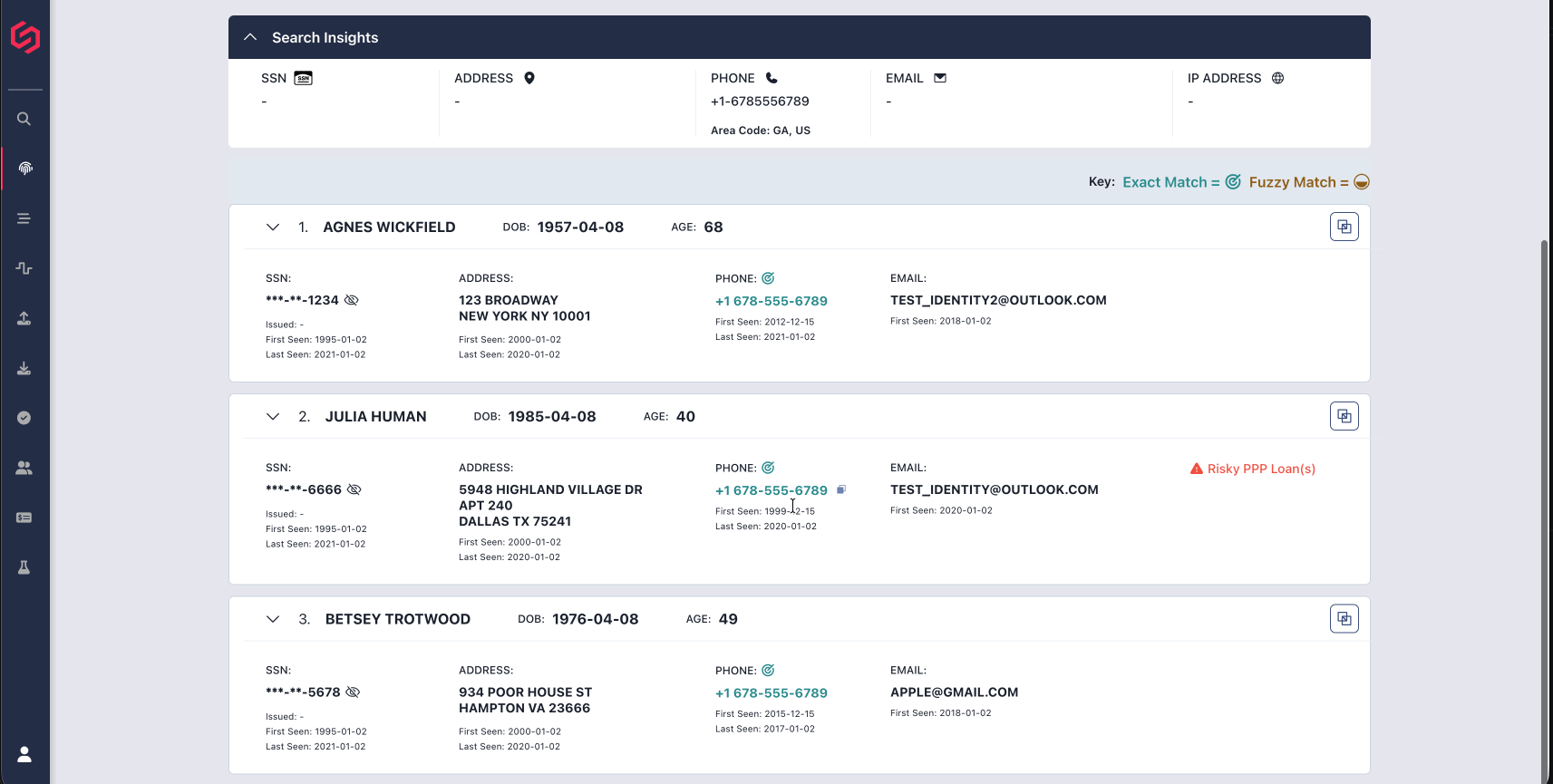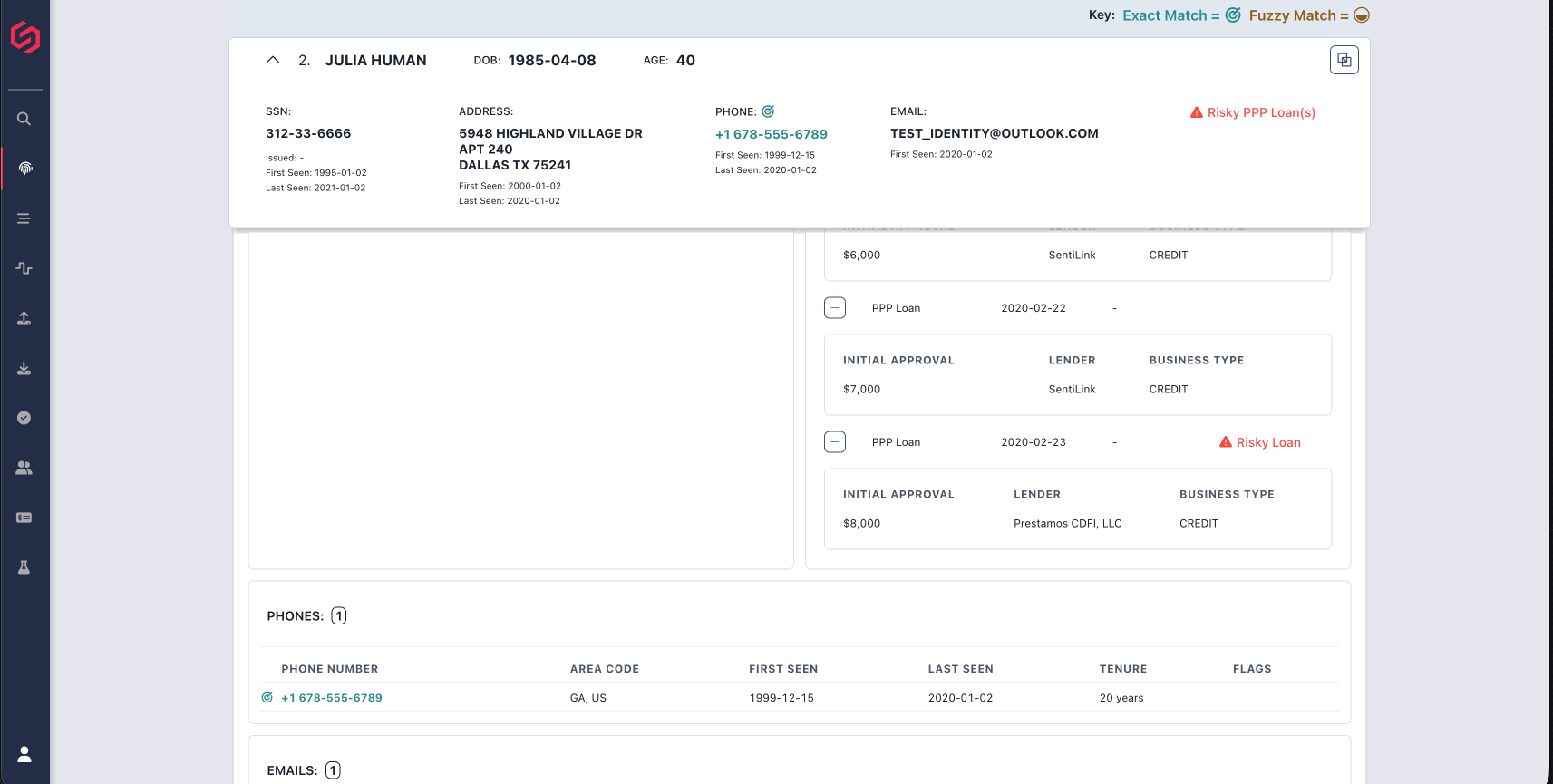
Blog article
February 19, 2026
Introducing SentiLink Intercept: Precision Tools for High Stakes Fraud Decisions
Read article
Blog article
December 2, 2025