Blog post
Using IP Address Data to Prevent ID Theft
SentiLink
Published
November 28, 2023

Fraud prevention solutions succeed on the strength of the data underpinning their models. The more data available and the greater the quality of that data, the more precisely a model or rules system can differentiate legitimate identities from fake or stolen ones. IP addresses are increasingly seen as a valuable tool in the fraud fighter's arsenal. When individuals were primarily applying in-person at a branch, determining if the person is who they say they are was a simpler process. However, now that more consumers are applying digitally, IP addresses are often just as important as other PII application elements.
IP address signals at the point of application
An IP address, when used in combination with personal information, can provide an additional layer of insights to inform fraud risk decisioning without introducing friction for consumers. The IP address itself can be useful for deriving behavioral signals such as velocity of applications coming from the same address, while IP address metadata can be used with other PII to identify fraudulent behavior.
Examples of IP address data relevant for fraud risk decisioning:
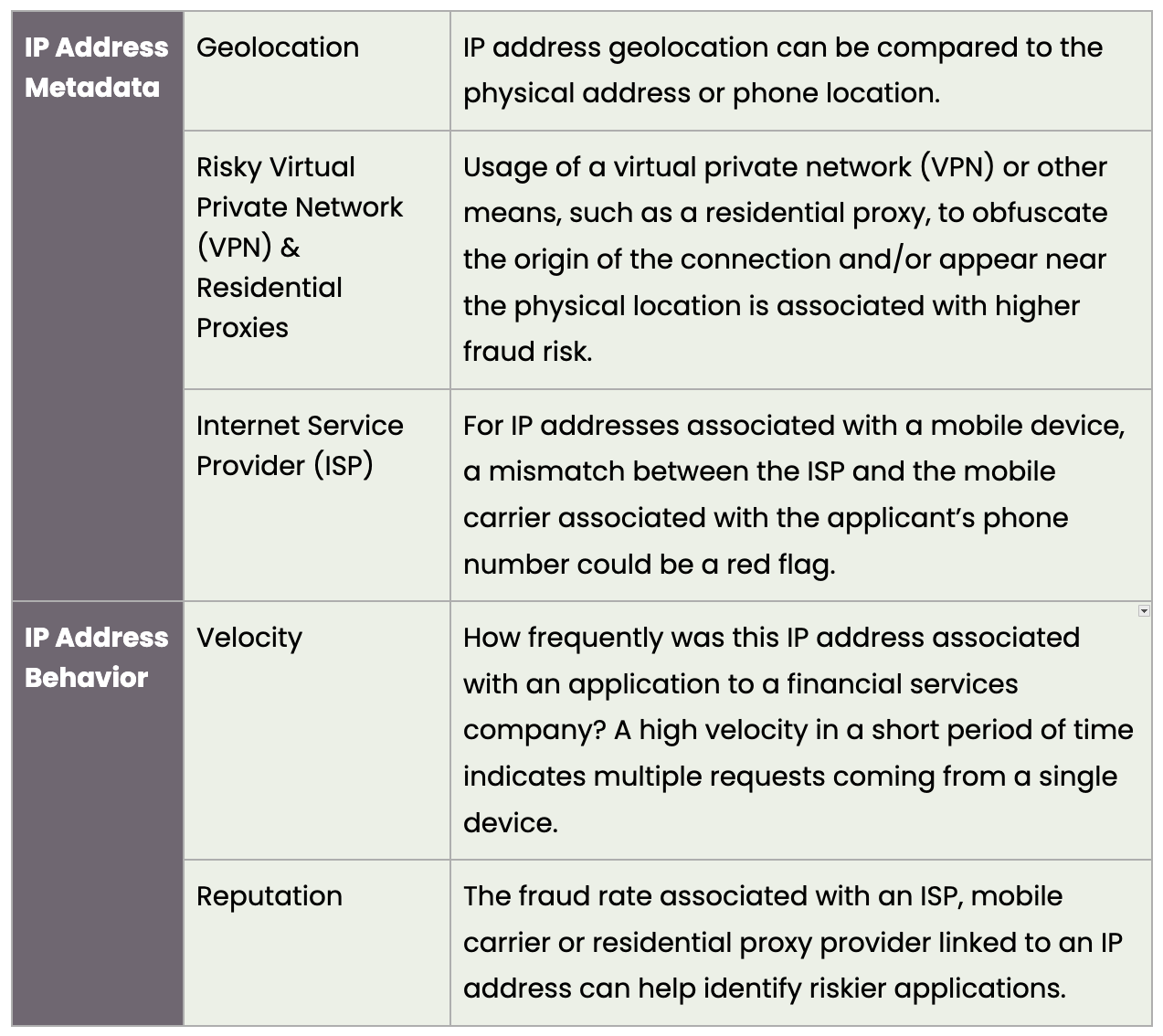 Note that VPN usage alone is not a reason to flag an application as fraudulent. While it is true the use of these services can indicate higher risk, VPN usage is not always malicious. With the widespread availability of consumer-grade VPN services, many individuals opt to protect their privacy using these services. As a result, it is important to review other factors when determining the risk of an application that is using a VPN.
Note that VPN usage alone is not a reason to flag an application as fraudulent. While it is true the use of these services can indicate higher risk, VPN usage is not always malicious. With the widespread availability of consumer-grade VPN services, many individuals opt to protect their privacy using these services. As a result, it is important to review other factors when determining the risk of an application that is using a VPN.
Residential proxies can be evaluated differently. While there are legitimate use cases, these use cases are typically limited to specialized practices within certain industries (e.g., simulating real user behavior to verify ad placement and appearance on a website, or managing multiple social media accounts without tripping platform security measures). Residential proxies find much less legitimate use when used to apply for a financial product. As a consequence, proxies can be scrutinized more readily when used to submit an application to a financial institution.
Solutions for fraudulent use of IP addresses
Insights from IP addresses become especially effective when coupled with solutions designed to harness the true value of these signals. SentiLink builds products to defend against identity theft that are tailored to the needs of our partners and grounded in the deep understanding of our Fraud Intelligence Team.
The SentiLink ID Theft Score indicates the likelihood that an incoming application is from a third party using stolen PII from a real person along with an email, phone, or address that is controlled by someone other than the owner of the PII. The underlying model uses a combination of metadata and behavioral IP address signals to deliver industry-leading performance. Examples of IP-related features used in the model include the following:
Geolocation:
- min_ip_address_distance_from_any_address_ip_address – Minimum distance between application IP address and applicant's historical addresses.
- is_ip_address_non_usa_ip_address – Whether the IP address is located outside the USA.
VPN:
- is_high_risk_vpn_ip_address – Whether the IP address is a risky VPN type.
Velocity:
- num_apps_short_succession_ip_cluster – Number of applications associated with the IP address in the past day.
Reputation:
- isp_risk_weight_ip_address – Risk score associated with the IP address ISP.
Likewise, SentiLink Facets offer IP-related attributes that can be used to enforce business policies such as filtering out applications where an IP address is located outside of the United States. Examples of IP-related attributes we offer include the following:
Geolocation:
- ip_distance_from_address_km – Distance between application address and application IP address.
- phones_pct_matching_ip_location – Fraction of phones in the IP address cluster with area codes that match the IP address location.
- ip_min_distance_to_addresses_on_record_km – Minimum distance between application IP address and applicant's historical addresses.
- ip_under_160km_from_known_address – Whether the distance between application IP address and application address is under 160km and the address can be verified as legitimate.
- phone_ip_state_match – Whether the IP address state location matches the phone state.
Velocity:
- ip_num_identities_cluster – Number of distinct consumers in the IP address cluster.
- ip_velocity_1y_cluster – Number of applications associated with the IP address over the past year.
- ip_velocity_1d_cluster – Number of applications associated with the IP address in the past day.
- ip_count_cluster – Number of applications at the same IP address.
- ip_ratio_seen_in_past_30d_cluster – Ratio of all applications that were seen with the application IP address in the past 30 days.
Our team of experts actively evaluate residential proxies and ISP mismatches during manual investigations and case labeling to inform future development of our products.
Conclusion
With the powerful signals that IP address metadata and behavior provide, organizations have a valuable tool to catch identity theft. As we continuously improve the effectiveness of our solutions here at SentiLink, we consistently seek out new and impactful signals to detect third party fraud. In fact, a study of partner usage revealed that those who include IP addresses with incoming application data when calling the ID Theft Score resulted in a 2.9% increase in model recall without any loss of precision.
For more information or help in preventing identity theft, you can get in touch with us here.
Related Content
.png)
Blog article
February 20, 2026
Romance Fraudsters Have Found a New Target: Your Home Equity
Read article
Blog article
February 19, 2026
Introducing SentiLink Intercept: Precision Tools for High Stakes Fraud Decisions
Read article
Blog article
December 2, 2025