Blog post
Using Email Data To Prevent ID Theft
Max Blumenfeld, Co-Founder, COO and Head of R&D
Published
June 30, 2021

Managing risk at onboarding requires an ability to validate identity data in real-time. When evaluating email data to prevent fraud, email domain, type and age are key signals.
The billions in unemployment benefits fraud highlight the importance of a comprehensive strategy in assessing emails at account opening.
Suspicious emails were used to both secure unemployment funds from the states and then launder them through DDA accounts opened using stolen credentials.
- A fraud ring that targeted WA’s unemployment benefits, for example, used disposable Yopmail accounts and Gmail aliases as part of their scheme to steal money.
- At SentiLink, we analyzed the emails used to open DDA accounts with stolen credentials receiving unemployment benefits at one of our partners and found that 2.3% had Gmail aliases using the same handle with a different number of dots to avoid being detected through linking.
Both disposable Yahoo emails and Gmail aliases are associated with higher risk. With Yahoo emails, we’ve seen time periods with some of our partners where upwards of 90% of applicants using disposable Yahoo emails were instances of ID theft. As for Gmail aliases, an increasing number of dots in the handle comes with increasing risk. At SentiLink, we’ve found that one or even two dots in the email handle presents comparable risk to the general population. The majority of applications we see with four or more dots are fraudulent.
This post describes strategies to analyze email domain, type and age to prevent ID theft.
Risky email domains
Most financial institutions blacklist every known risky email domain. Mail.com is a good place to start as they are frequently used by criminals to establish new emails. They have over 250 domains in categories including Jobs (accountant.com), Hobbies (birdlover.com), Tech (engineer.com), Music (ACDCFan.com), USA (Californiamail.com), World (Africamail.com), and Spiritual (Religious.com).
Yopmail is another risky disposable email generator worth blacklisting. There’s no need to create an account, a new address is auto generated, and it's as simple as typing in the email handle to access the inbox.
Measuring rates of fraud related to email domains is a further refinement to this blacklist. At SentiLink, we calculate a ratio of fraudulent apps to good apps for every risky email domain.
Ongoing manual review and evaluation keeps this list up to date. As new domains come online and appear on incoming applications, ideally those domains are monitored manually to determine the level of risk and whether to add them to the blacklist. Any brand new email domain is reason for concern.
Disposable and alias emails
As financial institutions have leaned into clustering and linking technology to identify fraudulent apps connected to the same email, many criminals have pivoted into creating disposable and alias emails to evade this fraud prevention technique.
While frequently used by criminals, disposable and alias emails are promoted by two of the biggest email domains, Google and Yahoo, as features for their users.
Linking together disposable and alias emails unlocks the ability to efficiently determine legitimate ones from the fraudulent ones.The most effective clustering strategies incorporate nuances related to disposable and alias emails.
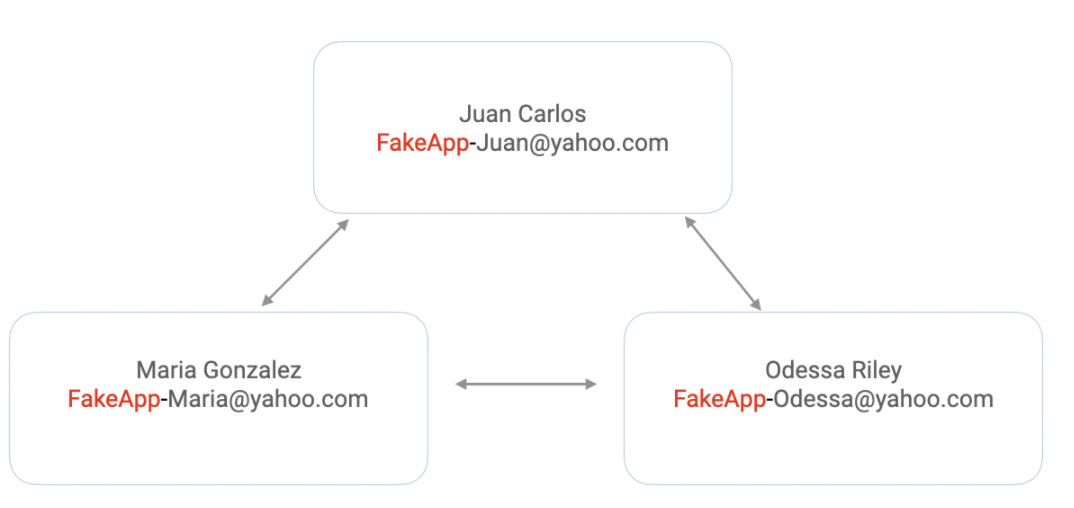
Yahoo disposable emails consist of a base name and a keyword. All addresses created will be structured as basename-keyword@yahoo.com. The base name can only be set up once and must be unique so all addresses will share the same base name. For emails with Yahoo domain, clustering on basename will enable you to catch criminals submitting multiple apps with different stolen credentials and effectively the same Yahoo email.
This base name for disposable Yahoo email addresses does need to be different from the account’s username. So, it’s not possible to strip out the last part of the email and cluster with the consumer’s original email.
With Google, users can create a new email alias by adding a period anywhere in the address or by adding a plus and typing any text after it. For example, a simple alias for the email, shawnasmith123@gmail.com, could be sh.aw.nas.mit.h123@gmail.com and shawnasmith123+45678@gmail.com. For the purposes of clustering, all three versions should be considered the same email.
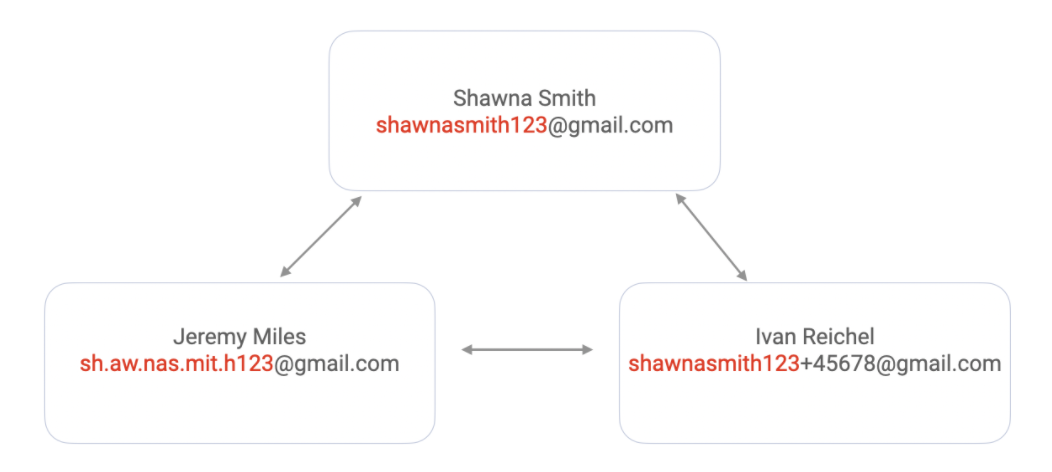
Any emails sent to the version with the plus sign or period in it will go to the inbox for shawnasmith123@gmail.com. Custom Gmail filters can be set up for each email alias, so emails to those addresses are automatically archived with particular labels.
Email and domain age
A newly created email domain is typically an indicator of fraud. We’ve seen cases at SentiLink where a fraudster creates a new email with a domain that appears to be connected to the victim’s previous business. The knowledge that it was a newly established domain helped to alert us to fraud.
Email age is usually a similarly reliable signal, but we’re seeing emails being used on applications with stolen credentials that have been used for a year or more.
For example, we saw a cluster of DDA applications using stolen credentials at several of our partners in April 2021 that used the same email address that was first established in July 2019. Fraudsters are aware that financial institutions are looking for consistent email usage.
As such, email age by itself is not reliable to prevent identity theft or to confirm a legitimate consumer.
Conclusion
Risk tolerance and resources drive treatment strategies when detecting suspicious emails. For certain high risk domains, some financial institutions may have processes to reject applications that include them. It is highly unlikely that someone using a certain known high risk email domain when applying for a deposit or credit account is legitimate. Others simply use the presence of email attributes as a high risk signal in their machine learning models.
For more information or help in preventing identity theft, you can get in touch with us here.
________________________________________

Max Blumenfeld is Co-founder and COO of SentiLink. Prior to SentiLink, Max led Risk Operations and Fraud Data Science at Affirm. Max holds a degree in mathematics and economics from the University of Chicago and was named to Forbes’ 30 Under 30 list in 2020.
Related Content
.png)
Blog article
February 20, 2026
Romance Fraudsters Have Found a New Target: Your Home Equity
Read article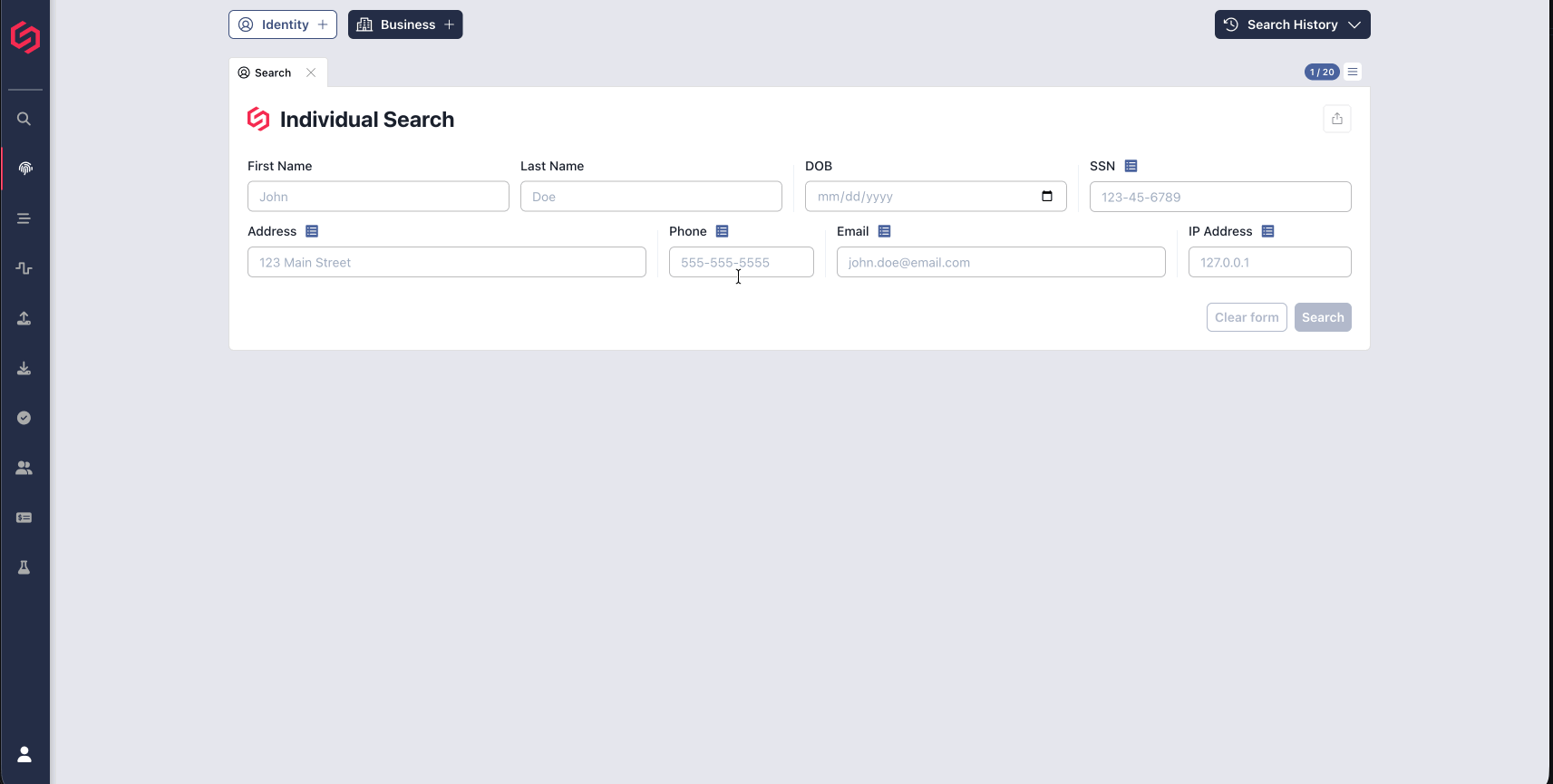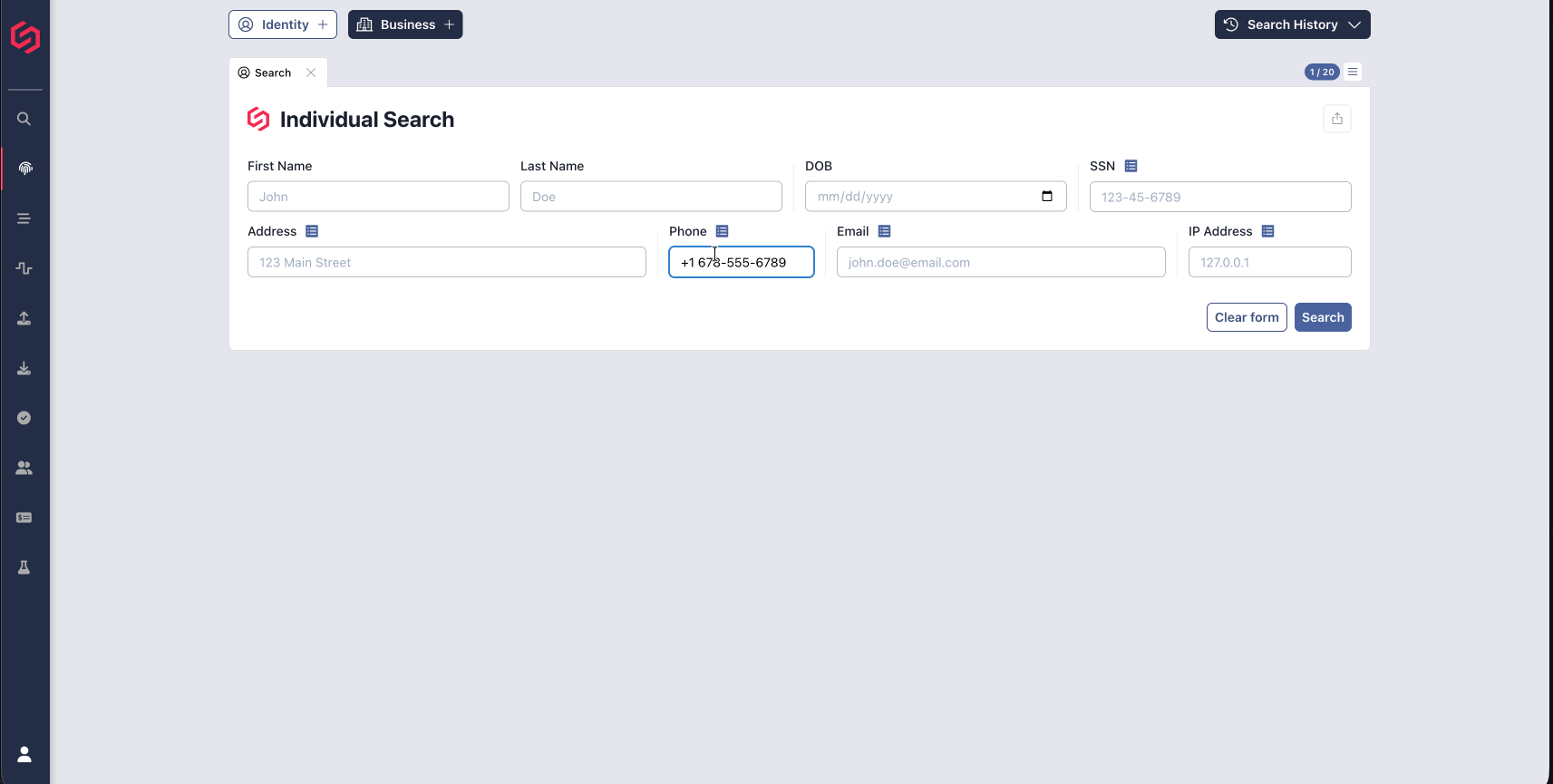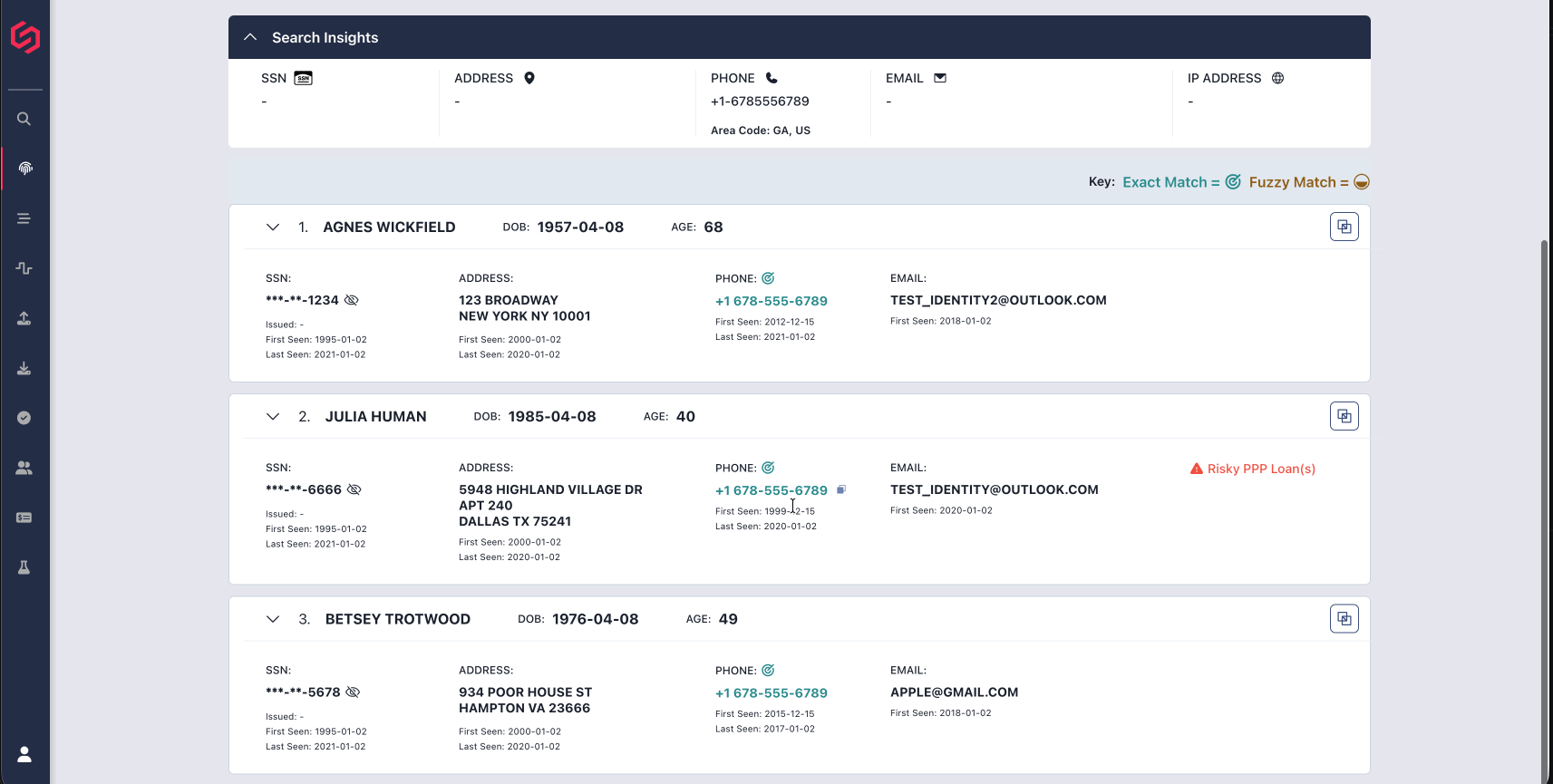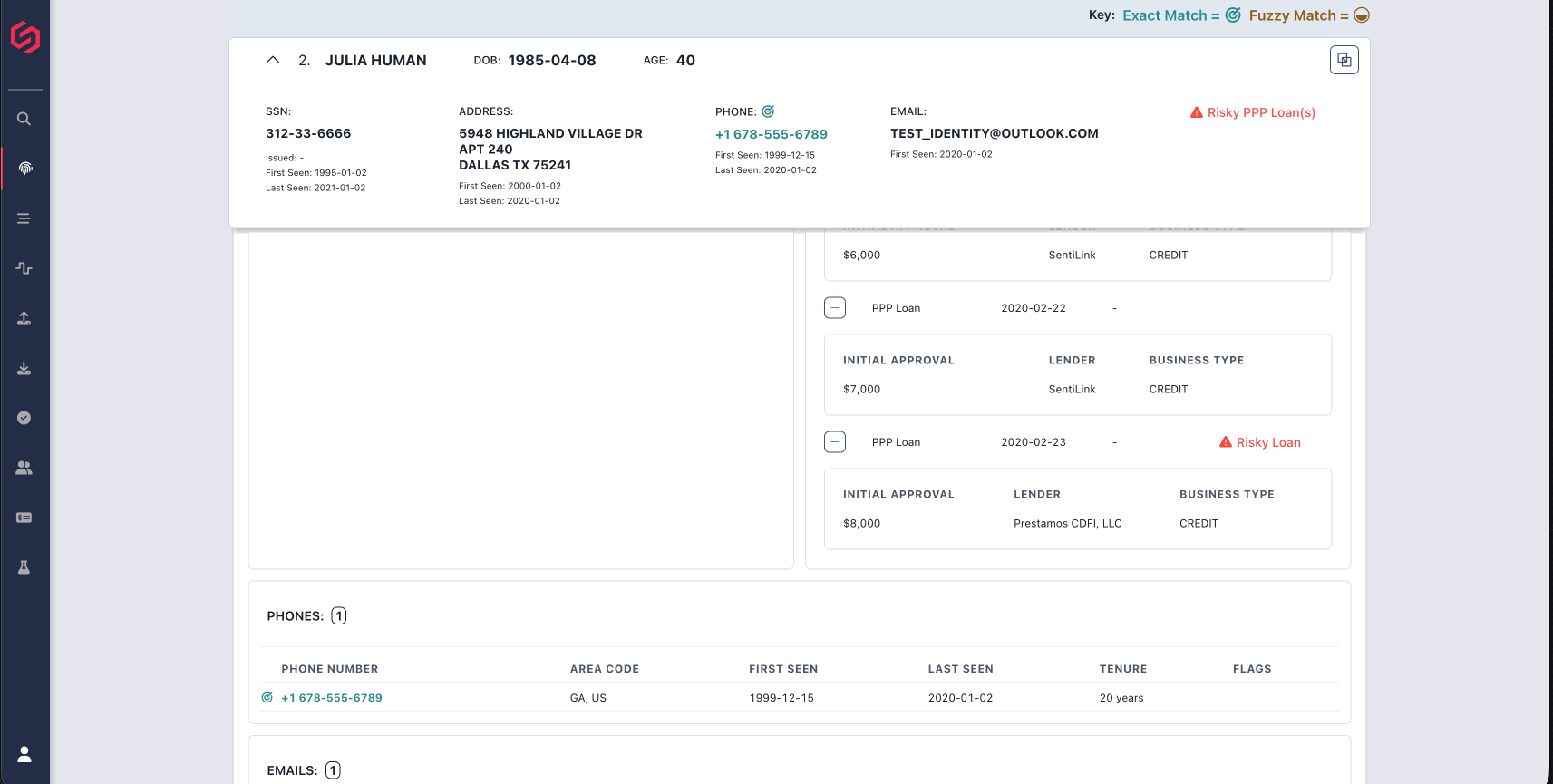
Blog article
February 19, 2026
Introducing SentiLink Intercept: Precision Tools for High Stakes Fraud Decisions
Read article
Blog article
December 2, 2025