Blog post
We analyzed $77M worth of stolen bank accounts. Here's what we found.
David Maimon
Published
January 29, 2025

This article is part of David Maimon's blog series Dark Corners: Research Notes From the Dark Web.
As SentiLink's Head of Fraud Insights, part of my job is keeping an eye on dark web markets, seedy Telegram channels, and other corners of the internet where we find the supply side for much of the fraud that SentiLink detects for our partners later down the line.
Since July of 2024, we've been monitoring a group of Telegram channels known to serve as markets for fraudsters – the same channels where we've found hundreds of millions of dollars in stolen checks. These markets are used to sell a variety of fraud "products," including stolen bank accounts, which fraudsters often advertise using screenshots to demonstrate they have access to, and control of, the victim's online banking. In just six months, we've catalogued 2,463 stolen accounts, with a total compromised balance of nearly $77 million.
What we found
To date, we've catalogued 2,463 unique compromised bank accounts shared across 46 different fraudulent Telegram channels, with a total compromised balance of $76,961,664.18. The first account we catalogued was posted on July 29, 2024, and as of this writing the most recent account we've catalogued was posted on January 22, 2025.
How did fraudsters get access to these accounts?
Scammers generally get access to target bank accounts via successful phishing or smishing campaigns.
Specifically, scammers will compose fake email and text messages which seem like they are associated with the victim's financial institutions, and then will send these emails and text messages to the victim along with a link. The text in these emails and SMS messages will notify the target of suspicious activity on their bank account, prompting them to review the activity by clicking a link in the email or text. When the link is clicked, the victim is routed to a scam page, a lookalike of the victim's real bank website.
On this page, they'll be prompted to log in (providing the fraudster their bank username and password), and they're often asked to provide a range of additional personal information, including uploading a picture of their drivers license. This gives the fraudsters full access to their bank accounts, as well as materials and information to "prove" that they are the account owner.
In some cases, scammers will use tools such as remote desktop protocol (RDP) as part of their operation. This tool allows scammers to connect to the victim’s business or home network, and then use the victim’s own network to access the bank account. By using these types of tools, scammers make it significantly harder for the bank's security team to detect the account takeover.
 Above: example of a phishing text message.
Above: example of a phishing text message.
How were the stolen bank accounts shared?
Fraudsters sell access to stolen accounts like these by posting about them, providing a price and a screenshot of the victim's online banking environment to demonstrate their access and to show the available account balances. From these screenshots, we are able to collect details such as the victim name, bank name, account type, and total balances available.
While some victims' accounts are posted just once, others had their accounts posted for sale repeatedly over the course of the roughly six months we've been monitoring – a few unlucky individuals had their accounts shared more than a dozen times over this period! (In the analysis that follows, though, we're counting each unique account just once. In cases where the same account has been shared multiple times, we are using the most recent account balance data for our calculations.)
 Above: a collage of screenshots posted by fraudsters to prove their access to stolen accounts. SentiLink has redacted these images; the fraudsters typically share them uncensored.
Above: a collage of screenshots posted by fraudsters to prove their access to stolen accounts. SentiLink has redacted these images; the fraudsters typically share them uncensored.
Where did the compromised accounts come from?
The compromised accounts come from 130 different banks, including most major banks and credit unions in the US. While we won't name specific banks, some of the country's largest banks were also the hardest-hit by fraudsters. One bank in particular had 1,121 accounts compromised – 45.5% of all the stolen accounts we catalogued – with a total compromised balance of more than $30 million.
What types of accounts were stolen?
Of the 2,463 compromised accounts we catalogued, 1,721 have account types such as "checking" or "savings" that can be easily identified from the fraudsters' screenshots, and 742 have generic or branded account type names such as "Advantage Banking" that make it difficult to label the account type. Of the 1,721 clearly-labeled accounts:
- 26.4% are checking accounts
- 24.6% are savings accounts
- 10.4% are Visa card accounts
- 3.8% are money market accounts
- 2% are MasterCard card accounts
- 1.4% are CDs
- 1.2% are IRAs
Whose accounts were stolen?
Our catalogue to date has 879 unique victims. Based on the names associated with the accounts, we believe that 772 of these victims (87.8%) are individuals and 106 of them (12%) are businesses.
The average victim in our data had 2.8 accounts compromised, but this is primarily because a few unlucky individuals and businesses had five or more accounts compromised. The median victim had two accounts compromised, which is not surprising – they're generally checking and savings accounts associated with the same bank.
In fact, even in the case of the outlier individuals and businesses who had five or more unique accounts compromised, in all cases these accounts were with the same bank. We did not find any instances of fraudsters having gained access to accounts at multiple banks for the same victim.
Perhaps unsurprisingly, businesses tended to have more money at stake in compromised accounts. For individuals, the average compromised total balance was $72,152 and the median compromised total balance was $16,950. For businesses, the average was $192,595 and the median was $36,731.
The averages are much higher than the medians because there were a few businesses and individuals with large balances at risk. The highest total balance for a single account was over $3.7 million, in the compromised accounts of a logging business. But it wasn't just businesses; several individuals with account balances totaling above $1M also had their accounts compromised.
How fraudsters use stolen accounts
Once fraudsters have access to a victim's online banking, they can use it in a variety of ways, including but not limited to:
Selling access. The accounts we analyzed were posted by fraudsters to sell to other fraudsters. Selling access to an account can generate quick profits and may not come with the same risks as actually attempting to withdraw money from those accounts, since neither the bank nor the victim is likely to be aware the account has been compromised until money is withdrawn from it. In many cases, the scammers sell access to both the account and the RDP tool, which gives the buyer access to the victim’s computer network and computers as well.
Using the accounts. Scammers can use their account access to steal the victim's funds. Most often, after studying the account history, the fraudsters extract money from the accounts with small transactions, which tend to fly under both the victim's and bank's radar.
Part of this account inspection also involves the fraudster searching for the victim's checks, images of which are often available in the account history. Those images can be used by the scammers to make forged checks that draw from the victim's account.
Finally, and depending on the account functionality (for example, its Zelle capabilities), the fraudsters may use the accounts to send money to drop accounts under their control. This has the potential to bring a windfall of ill-gotten cash, but it's also much riskier, since the bank's anti-fraud measures could block the withdrawal. Even if it doesn't, the victim is certain to notice the crime, which also significantly increases the risk of being caught.
Leveraging the accounts as part of larger fraud schemes. Given the massive amount of information available to fraudsters as the result of data breaches, access to an individual or business's bank accounts could also be used as part of a variety of other fraud schemes such as identity theft, theft of additional accounts connected to the victim's bank account, opening new accounts in the victim's name, and money laundering. In fact, high balance and actively-used compromised accounts are particularly useful for money launderers since the frequent transactions in those accounts can allow the fraudsters to fly undetected for a long period of time.
What can financial institutions do?
It's clear that compromised accounts represent a major problem. Our analysis reflects just six months across a few dozen Telegram channels, and only highlights the stolen accounts that were actually put up for sale. The true scale of the problem is larger, as fraudsters also sell stolen accounts in places like the dark web, and many accounts may be compromised and used directly rather than being put up for sale.
What can financial institutions (FIs) do to combat these account takeovers?
First, FIs should strengthen the security of their online platforms using current industry best practices. For example, many banks still use SMS messages for MFA, and some don't use MFA at all. SMS 2FA has some glaring weaknesses; FIs should at least give customers the option of securing their accounts with options like OATH, security key, or push authentication.
FIs should also employ robust anti-fraud controls to detect fraud at account opening and throughout the life cycle of an account – ideally, the FI detects unusual access and is able to lock out the fraudster before their customer ever becomes a victim.
Related Content
.png)
Blog article
February 20, 2026
Romance Fraudsters Have Found a New Target: Your Home Equity
Read article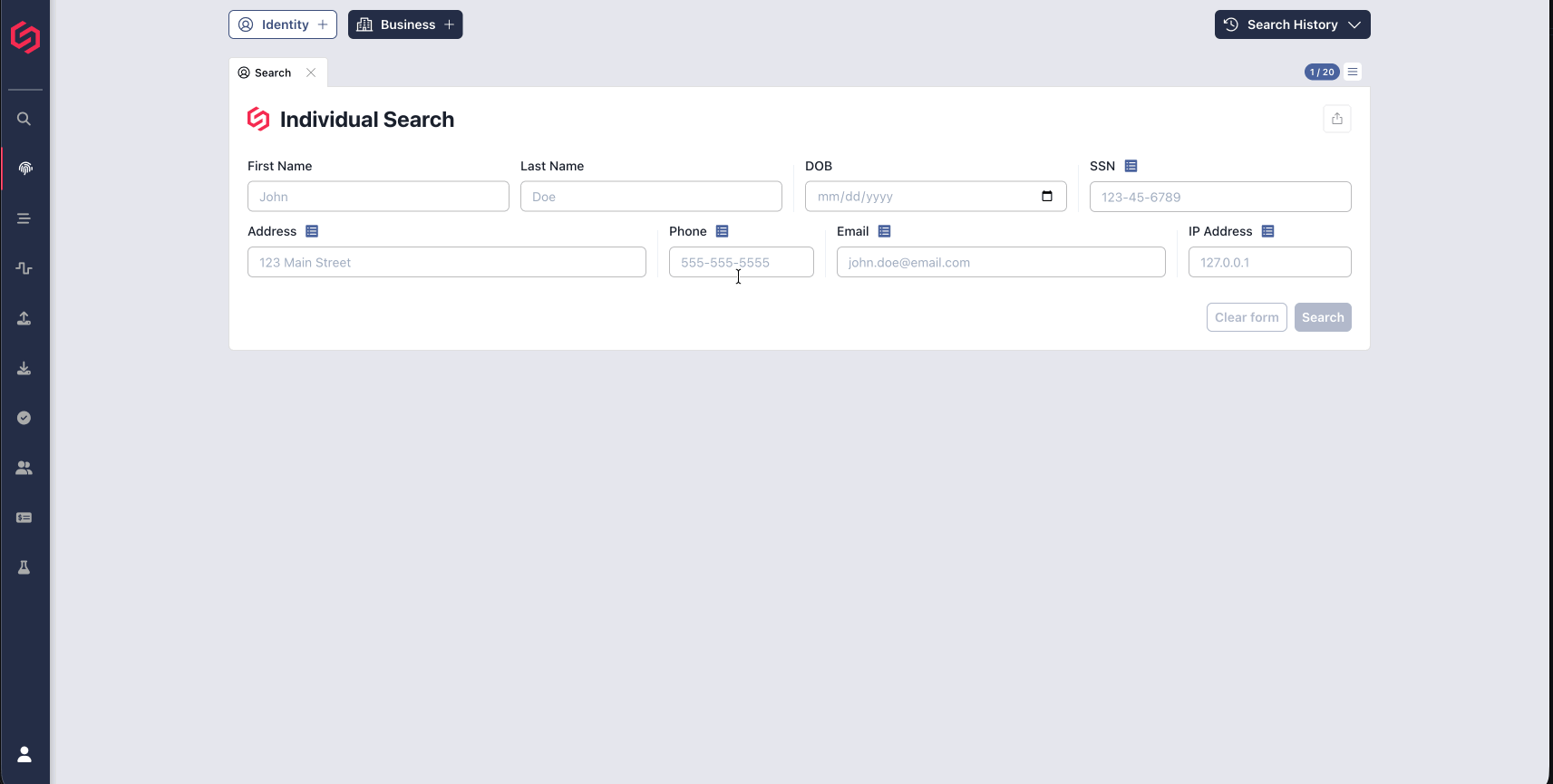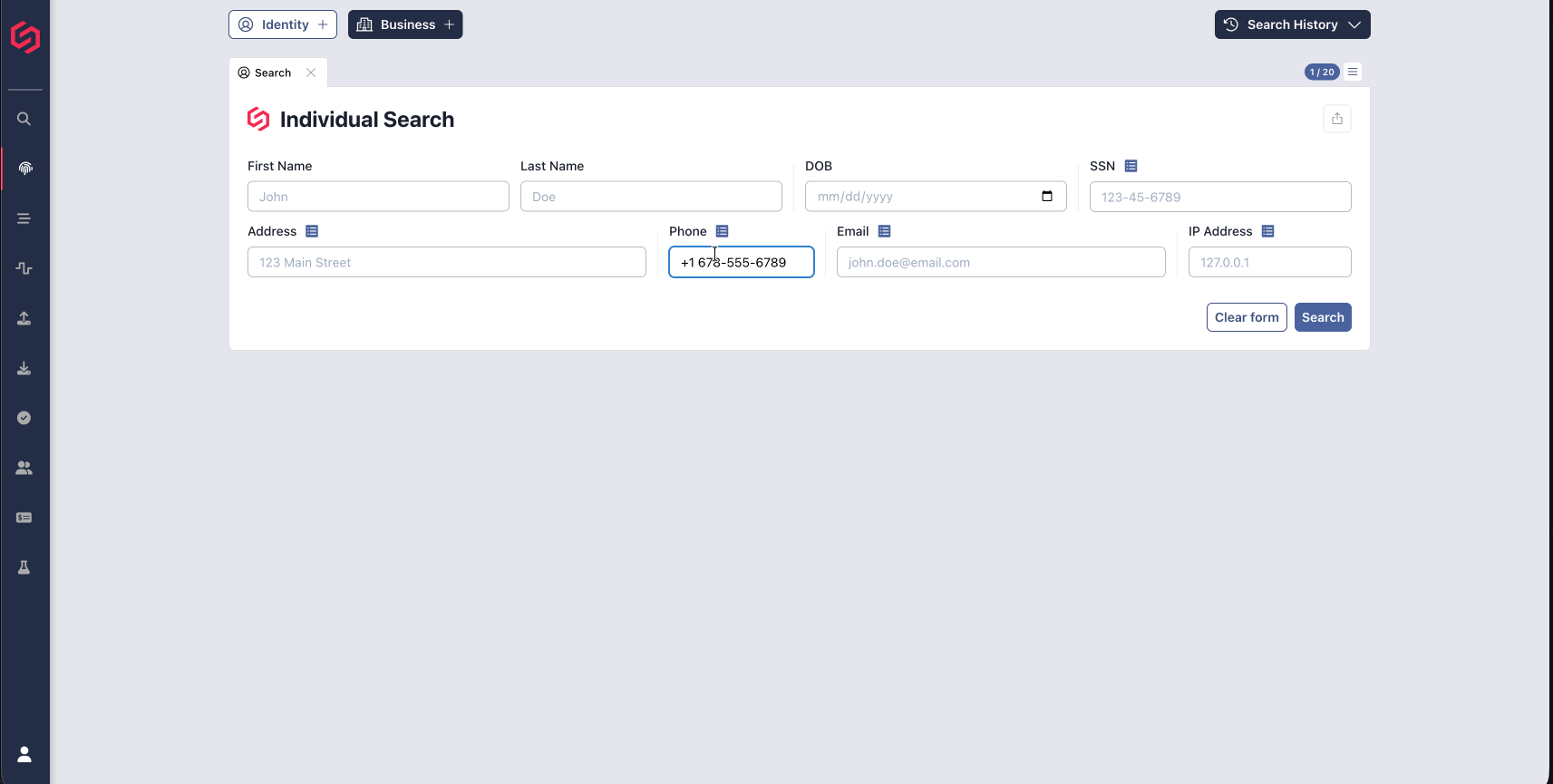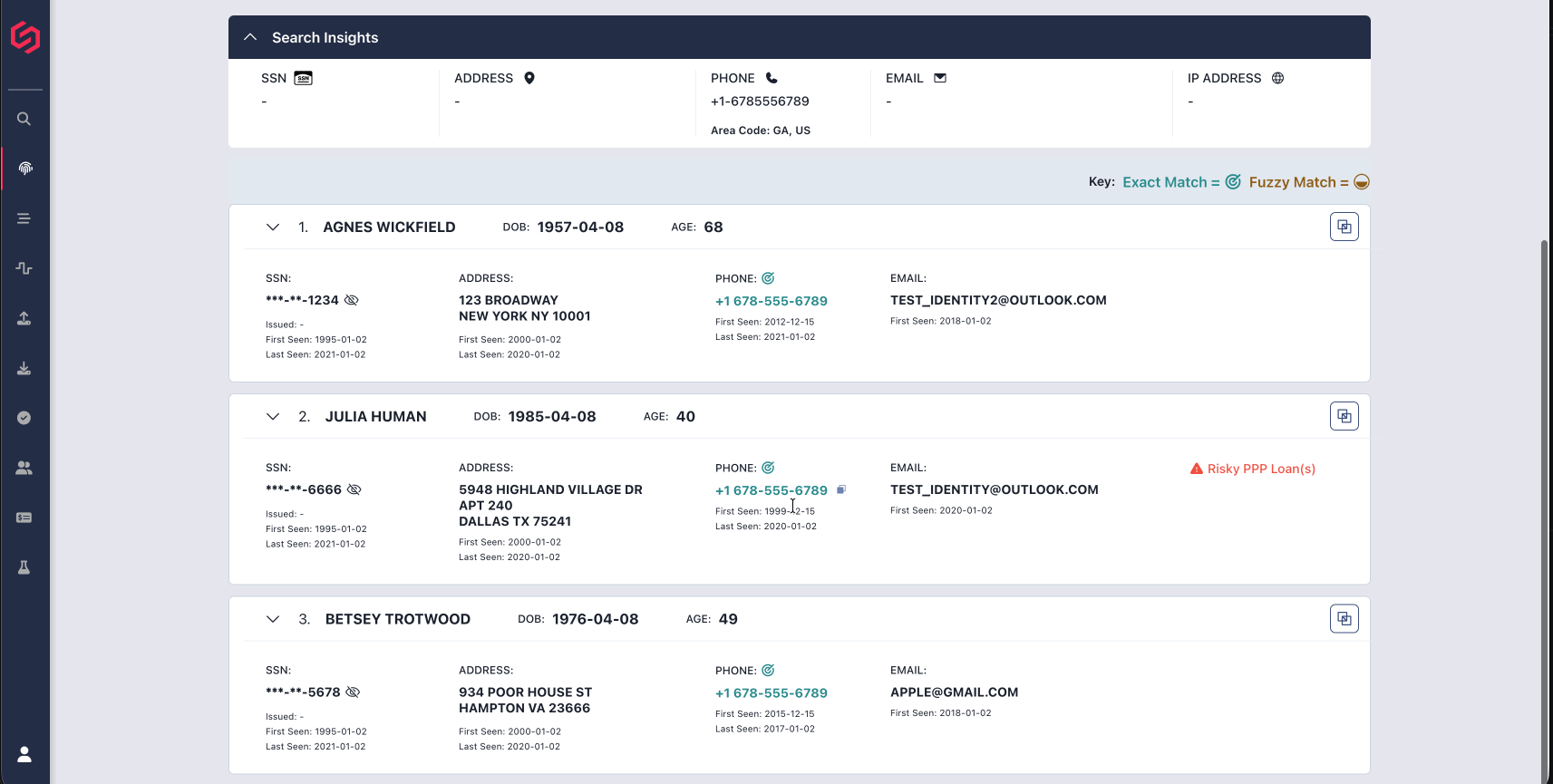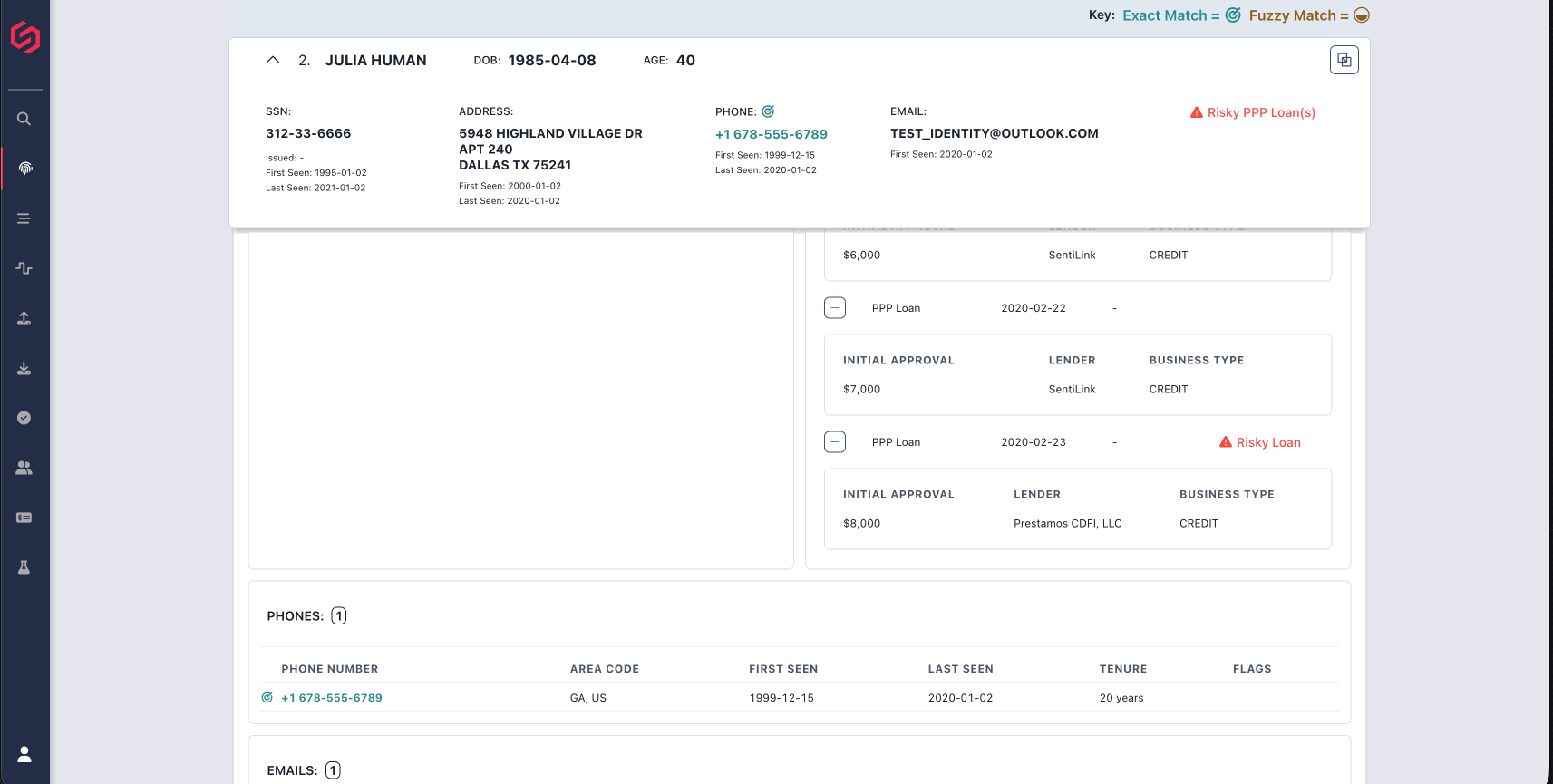
Blog article
February 19, 2026
Introducing SentiLink Intercept: Precision Tools for High Stakes Fraud Decisions
Read article
Blog article
December 2, 2025